Stop Data Leaks Now: How SASE with Integrated DLP Safeguards Your Critical Information

As organizations increasingly adopt cloud services and support remote work, protecting sensitive data has become more challenging than ever. Traditional data loss prevention (DLP) solutions often struggle with distributed environments where data flows across multiple channels and locations. MCK’s SASE solution with integrated DLP capabilities addresses these challenges by embedding comprehensive data protection directly into the network security fabric.

Key Takeaways
- Integrated DLP within SASE provides superior data protection compared to standalone solutions
- MCK’s solution offers content inspection and classification across all channels and locations
- AI-powered analysis reduces false positives while maintaining robust protection
- Automated compliance reporting simplifies regulatory adherence
- Unified management reduces complexity and operational overhead
- Contextual awareness improves accuracy of data protection policies
Understanding Modern DLP Requirements
Traditional DLP solutions were designed for environments where data primarily resided within corporate networks and moved through controlled channels. Today’s reality is vastly different—sensitive information flows through cloud services, collaboration platforms, personal devices, and home networks, creating numerous potential points of exposure.
This shift demands a new approach to data protection. Modern DLP must secure data regardless of location or channel while maintaining visibility across increasingly complex environments. It must also balance security with usability, preventing data leaks without impeding legitimate business activities.
MCK’s integrated DLP approach addresses these requirements by embedding data protection directly into the SASE framework. This integration ensures consistent policy enforcement across all channels while providing the contextual awareness needed for accurate detection and prevention.
MCK’s Integrated DLP Capabilities
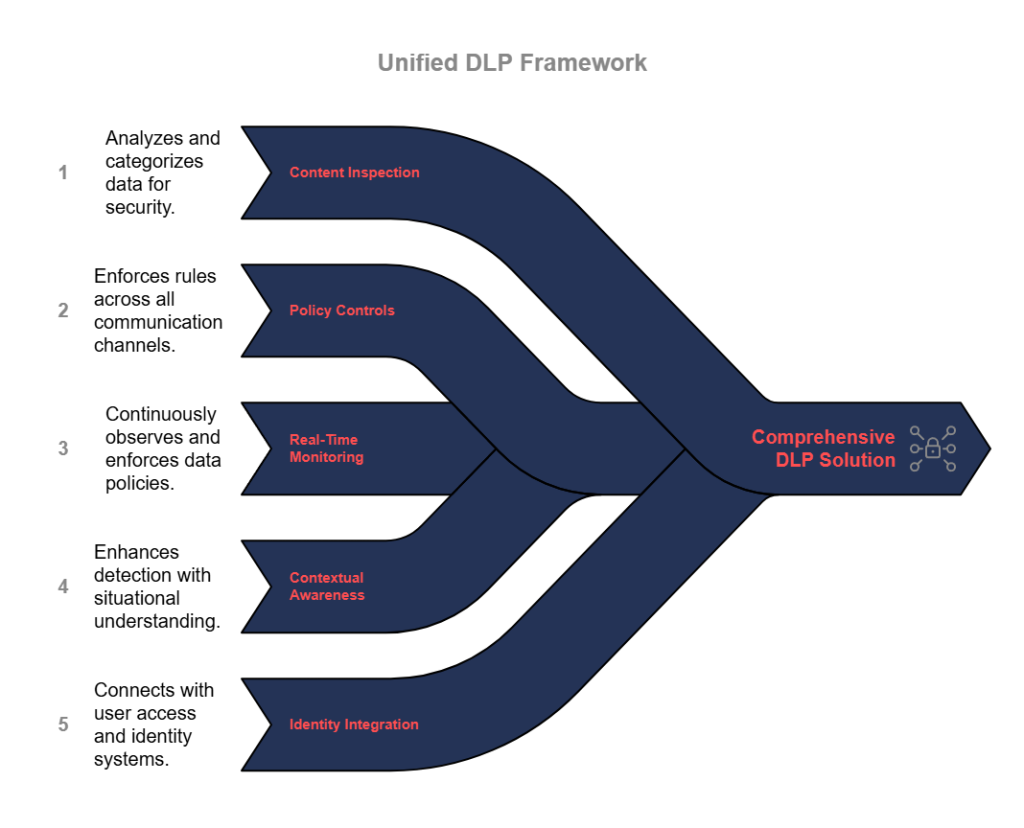
Content Inspection and Classification
At the core of MCK’s DLP capabilities is advanced content inspection that identifies sensitive data in real-time. The solution examines file content, not just metadata, using pattern matching, fingerprinting, and machine learning to recognize confidential information even when it’s embedded within complex documents.
Classification occurs automatically based on predefined policies, with options for both predefined categories (PII, financial data, intellectual property) and custom classifications specific to your organization’s needs. This classification drives appropriate protection measures based on data sensitivity and business context.
Policy-Based Controls Across All Channels
MCK’s solution applies consistent data protection policies across all communication channels, including:
- Web traffic and cloud applications
- Email and messaging platforms
- File transfers and downloads
- Endpoint activities
- Print and peripheral device usage
This comprehensive coverage eliminates protection gaps that occur when different channels are secured by separate solutions with inconsistent policies. The unified approach ensures that sensitive data receives appropriate protection regardless of how users access or share it.
Real-Time Monitoring and Enforcement
Unlike periodic scanning approaches, MCK’s integrated DLP monitors data movements in real-time, identifying potential violations as they occur. This immediate detection allows for prompt intervention before data leaves the protected environment.
Enforcement options range from passive monitoring and alerting to active blocking of unauthorized transfers. The platform supports graduated responses based on risk level, allowing organizations to balance security with business needs. For example, transfers containing customer information might trigger encryption requirements rather than outright blocking.
Contextual Awareness for Accurate Detection
MCK’s solution goes beyond simple pattern matching by incorporating contextual factors into detection algorithms. The system considers:
- User identity and role
- Device type and security posture
- Location and network characteristics
- Time and behavioral patterns
- Application being used
- Business justification
This contextual awareness significantly improves accuracy, reducing false positives while maintaining comprehensive protection. For example, the system can distinguish between a marketing employee legitimately sharing approved customer testimonials and an unauthorized attempt to extract the customer database.
Integration with Identity and Access Management
By integrating with identity and access management systems, MCK’s DLP solution applies appropriate policies based on user roles and permissions. This integration ensures that protection measures align with legitimate business needs while preventing unauthorized access or sharing.
The solution supports role-based access controls that determine what data users can access, modify, or share. These controls adapt dynamically as users move between roles or projects, ensuring appropriate protection without manual reconfiguration.
Implementation Across Key Data Channels
Securing Data in Transit
MCK’s SASE platform inspects all network traffic, identifying and protecting sensitive data as it moves between users, applications, and external parties. Strong encryption ensures that protected data remains secure even if intercepted, while granular controls prevent unauthorized sharing.
The solution supports both TLS inspection for encrypted web traffic and application-level controls for cloud services. This multi-layered approach ensures comprehensive protection without creating security blind spots.
Protecting Cloud Applications and Storage
As organizations increasingly rely on cloud services, protecting data within these environments becomes critical. MCK’s integrated CASB functionality extends DLP policies to cloud applications, monitoring uploads, downloads, and sharing activities for policy violations.
The platform provides visibility into shadow IT usage, identifying unauthorized cloud services that might bypass security controls. This discovery capability helps organizations address potential data leakage points before they result in breaches.
Endpoint Protection for Remote Devices
Remote and personal devices present particular challenges for data protection. MCK’s solution extends DLP policies to endpoints regardless of location, monitoring file operations and data transfers even when devices are disconnected from corporate networks.
The platform supports both agent-based protection for managed devices and agentless controls for BYOD scenarios. This flexibility ensures appropriate protection based on device ownership and management status.
Email and Collaboration Tool Security
Email remains a primary vector for data leakage, whether through accidental sharing or malicious exfiltration. MCK’s DLP capabilities scan outbound emails and attachments, identifying sensitive content before it leaves the organization.
The solution also extends to modern collaboration platforms like Teams, Slack, and Zoom, monitoring file sharing and communications within these tools. This coverage addresses a significant gap in many traditional DLP deployments that focus primarily on email and web traffic.
Compliance Benefits
Meeting Regulatory Requirements
MCK’s integrated DLP helps organizations meet regulatory requirements across various frameworks, including GDPR, HIPAA, PCI DSS, and industry-specific regulations. Predefined policy templates address common compliance needs, while customization options accommodate unique requirements.
The solution’s comprehensive coverage ensures that regulated data receives appropriate protection regardless of location or channel. This consistent protection simplifies compliance efforts by eliminating the need to implement different controls for different environments.
Automated Compliance Reporting
Demonstrating compliance requires comprehensive documentation of protection measures and their effectiveness. MCK’s solution automates this reporting process, generating detailed records of policy enforcement, potential violations, and remediation actions.
Customizable reports address specific regulatory requirements, providing the evidence needed for audits and assessments. This automation reduces the administrative burden of compliance while improving accuracy and completeness.
Audit Trail Capabilities
MCK’s platform maintains detailed audit trails of all data access and movement, creating an immutable record for investigation and compliance purposes. These logs capture user actions, policy applications, and system responses, providing complete visibility into data handling practices.
Advanced search capabilities allow security teams to quickly locate relevant events during investigations or audits. This rapid access to historical information accelerates response times and improves overall security posture.
Operational Advantages
Simplified Management Through Single Console
MCK’s unified management interface provides comprehensive visibility and control across all DLP functions. Security teams can define policies, monitor activities, and respond to alerts from a single console, eliminating the need to switch between multiple tools.
This consolidated approach reduces administrative overhead while improving consistency. Policy changes apply immediately across all channels, ensuring uniform protection without manual synchronization between separate systems.
Reduced False Positives Through AI-Powered Analysis
False positives represent a significant challenge for traditional DLP solutions, often leading to alert fatigue and reduced effectiveness. MCK’s AI-powered analysis significantly reduces these false alarms by incorporating contextual information and learning from past decisions.
The system continuously improves its detection accuracy through machine learning, adapting to organization-specific data patterns and user behaviors. This adaptive approach maintains robust protection while minimizing disruption to legitimate business activities.
Scalability for Growing Businesses
As a cloud-native solution, MCK’s integrated DLP scales effortlessly to accommodate changing business needs. Organizations can extend protection to new users, locations, and data types without infrastructure changes or complex reconfiguration.
This scalability makes the solution particularly valuable for growing businesses or those with seasonal fluctuations in activity. Protection remains consistent regardless of scale, ensuring that security keeps pace with business evolution.
Talk to a SASE Expert Today
Ready to transform your approach to data protection with an AI-powered SASE solution that includes integrated DLP capabilities? MCK’s team of SASE experts can help you design and implement a custom solution that addresses your specific data security challenges while optimizing network performance.
Contact MCK today to schedule a consultation and discover how our Unified SASE solution with integrated DLP can help you achieve more effective data protection across your entire organization. Our experts will work with you to develop a personalized implementation plan that aligns with your compliance requirements and business goals, ensuring comprehensive protection for your sensitive information regardless of where it resides or how it’s accessed.
